 Your new post is loading...
 Your new post is loading...
No one's better at hacking than the NSA. And now one if its powerful tools is available to everyone for free. The National Security Agency develops advanced hacking tools in-house for both offense and defense—which you could probably guess even if some notable exampleshadn't leaked in recent years. But on Tuesday at the RSA security conference in San Francisco, the agency demonstrated Ghidra, a refined internal tool that it has chosen to open source. And while NSA cybersecurity adviser Rob Joyce called the tool a "contribution to the nation’s cybersecurity community" in announcing it at RSA, it will no doubt be used far beyond the United States. You can't use Ghidra to hack devices; it's instead a reverse-engineering platform used to take "compiled," deployed software and "decompile" it. In other words, it transforms the ones and zeros that computers understand back into a human-readable structure, logic, and set of commands that reveal what the software you churn through it does. Reverse engineering is a crucial process for malware analysts and threat intelligence researchers, because it allows them to work backward from software they discover in the wild—like malware being used to carry out attacks—to understand how it works, what its capabilities are, and who wrote it or where it came from. Reverse engineering is also an important way for defenders to check their own code for weaknesses and confirm that it works as intended. "If you’ve done software reverse engineering, what you’ve found out is it’s both art and science; there’s not a hard path from the beginning to the end," Joyce said. "Ghidra is a software reverse-engineering tool built for our internal use at NSA. We're not claiming that this is the one that’s going to be replacing everything out there—it's not. But it helped us address some things in our workflow." Similar reverse-engineering products exist on the market, including a popular disassembler and debugger called IDA. But Joyce emphasized that the NSA has been developing Ghidra for years, with its own real-world priorities and needs in mind, which makes it a powerful and particularly usable tool. Products like IDA also cost money, whereas making Ghidra open source marks the first time that a tool of its caliber will be available for free—a major contribution in training the next generation of cybersecurity defenders. (Like other open source code, though, expect it to have some bugs.) Joyce also noted that the NSA views the release of Ghidra as a sort of recruiting strategy, making it easier for new hires to enter the NSA at a higher level or for cleared contractors to lend their expertise without needing to first come up to speed on the tool. The NSA announced Joyce’s RSA talk, and Ghidra’s imminent release, in early January. But knowledge of the tool was already public thanks to WikiLeaks’ March 2017 “Vault 7” disclosure, which discussed a number of hacking tools used by the CIA and repeatedly referenced Ghidra as a reverse-engineering tool created by the NSA. The actual code hadn’t seen the light of day, though, until Tuesday—all 1.2 million lines of it. Ghidra runs on Windows, MacOS, and Linux and has all the components security researchers would expect. But Joyce emphasized the tool's customizability. It is also designed to facilitate collaborative work among multiple people on the same reversing project—a concept that isn't as much of a priority in other platforms. Ghidra also has user-interface touches and features meant to make reversing as easy as possible, given how tedious and generally challenging it can be. Joyce's personal favorite? An undo/redo mechanism that allows users to try out theories about how the code they are analyzing may work, with an easy way to go back a few steps if the idea doesn't pan out. The NSA has made other code open source over the years, like its Security-Enhanced Linux and Security-Enhanced Android initiatives. But Ghidra seems to speak more directly to the discourse and tension at the heart of cybersecurity right now. By being free and readily available, it will likely proliferate and could inform both defense and offense in unforeseen ways. If it seems like releasing the tool could give malicious hackers an advantage in figuring out how to evade the NSA, though Dave Aitel, a former NSA researcher who is now chief security technology officer at the secure infrastructure firm Cyxtera, said that that isn't a concern. “Malware authors already know how to make it annoying to reverse their code,” Aitel said. “There’s really no downside” to releasing Ghidra. No matter what comes next for the NSA's powerful reversing tool, Joyce emphasized on Tuesday that it is an earnest contribution to the community of cybersecurity defenders—and that conspiracy theorists can rest easy. "There’s no backdoor in Ghidra," he said. "Come on, no backdoor. On the record. Scout's honor."
Internet paranoiacs drawn to bitcoin have long indulged fantasies of American spies subverting the booming, controversial digital currency. Increasingly popular among get-rich-quick speculators, bitcoin started out as a high-minded project to make financial transactions public and mathematically verifiable — while also offering discretion. Governments, with a vested interest in controlling how money moves, would, some of bitcoin’s fierce advocates believed, naturally try and thwart the coming techno-libertarian financial order. It turns out the conspiracy theorists were onto something. Classified documents provided by whistleblower Edward Snowden show that the National Security Agencyindeed worked urgently to target bitcoin users around the world — and wielded at least one mysterious source of information to “help track down senders and receivers of Bitcoins,” according to a top-secret passage in an internal NSA report dating to March 2013. The data source appears to have leveraged the NSA’s ability to harvest and analyze raw, global internet traffic while also exploiting an unnamed software program that purported to offer anonymity to users, according to other documents. Although the agency was interested in surveilling some competing cryptocurrencies, “Bitcoin is #1 priority,” a March 15, 2013 internal NSA report stated. The documents indicate that “tracking down” bitcoin users went well beyond closely examining bitcoin’s public transaction ledger, known as the Blockchain, where users are typically referred to through anonymous identifiers; the tracking may also have involved gathering intimate details of these users’ computers. The NSA collected some bitcoin users’ password information, internet activity, and a type of unique device identification number known as a MAC address, a March 29, 2013 NSA memosuggested. In the same document, analysts also discussed tracking internet users’ internet addresses, network ports, and timestamps to identify “BITCOIN Targets.” The agency appears to have wanted even more data: The March 29 memo raised the question of whether the data source validated its users, and suggested that the agency retained bitcoin information in a file named “Provider user full.csv.” It also suggested powerful search capabilities against bitcoin targets, hinting that the NSA may have been using its XKeyScore searching system, where the bitcoin informationand wide range of other NSA data was cataloged, to enhance its information on bitcoin users. An NSA reference document indicated that the data source provided “user data such as billing information and Internet Protocol addresses.” With this sort of information in hand, putting a name to a given bitcoin user would be easy.
Heard of that presidential election coming up? Russia has too. And that worries US officials. WHAT'S GOING ON? Yesterday, the head of the NSA told lawmakers that he's worried a foreign government (hint: rhymes with Shmussia) may be trying to undermine the US election. The FBI is investigating two recent cyber attacks on voter registration databases in Illinois and Arizona that were traced back to Russia. Officials think more states might have been targeted, but their lips are sealed because classified. WHY IS THIS HAPPENING? Unclear. But this comes after the Democratic party was hacked earlier this year by groups believed to have ties to zee Russian government. The Clinton campaign thinks Russia hacked the Dems to benefit GOP nominee Donald Trump, who has given props to Russian President Putin many times on the campaign trail. Trump says Putin's not helping him, but he wouldn't mind if Russia did some more digginginto Clinton's inbox. ANYTHING ELSE? Yesterday, Russian hackers leaked the medical records of US Olympic athletes…including Serena Williams and Simone Biles. These records show that both ladies got the OK from officials to use banned drugs for medical reasons. The hackers said these records proved the athletes played "well but not fair." Reminder: dozens of Russian athletes were banned from Rio thanks to a state-sponsored doping scandal. Not the same thing. theSKIMM Many think all of these hacks are aimed at hurting the credibility of the US on the world stage. And the idea that Russia – a major geopolitical player – may be trying to manipulate the credibility of the US presidential race has some wondering when and how the US will respond.
|
The US National Security Agency will release a free reverse engineering tool at the upcoming RSA security conference that will be held at the start of March, in San Francisco. The software's name is GHIDRA and in technical terms, is a disassembler, a piece of software that breaks down executable files into assembly code that can then be analyzed by humans. The NSA developed GHIDRA at the start of the 2000s, and for the past few years, it's been sharing it with other US government agencies that have cyber teams who need to look at the inner workings of malware strains or suspicious software. GHIDRA's existence was never a state secret, but the rest of the world learned about it in March 2017 when WikiLeaks published Vault7, a collection of internal documentation files that were allegedly stolen from the CIA's internal network. Those documents showed that the CIA was one of the agencies that had access to the tool. According to these documents, GHIDRA is coded in Java, has a graphical user interface (GUI), and works on Windows, Mac, and Linux. GHIDRA can also analyze binaries for all major operating systems, such as Windows, Mac, Linux, Android, and iOS, and a modular architecture allows users to add packages in case they need extra features. According to GHIDRA's description in the RSA conference session intro, the tool "includes all the features expected in high-end commercial tools, with new and expanded functionality NSA uniquely developed." US government workers to whom ZDNet has spoken today said the tool is well-known and liked, and generally used by operators in defensive roles, who normally analyze malware found on government networks. Some people who know and used the tool and have shared opinions on social media, such as HackerNews, Reddit, and Twitter, have compared GHIDRA with IDA, a well-known reverse engineering tool -but also very expensive, with licenses priced in the range of thousands of dollars. Most users say that GHIDRA is slower and buggier than IDA, but by open-sourcing it, the NSA will benefit from free maintenance from the open source community, allowing GHIDRA to quickly catch up and maybe surpass IDA. The news of the NSA open-sourcing one of its internal tools should not surprise you. The NSA has open-sourced all sorts of tools over the past few years, with the most successful of them being Apache NiFi, a project for automating large data transfers between web apps, and which has become a favorite on the cloud computing scene. In total, the NSA has open-sourced 32 projects as part of its Technology Transfer Program (TTP) so far and has most recently even opened an official GitHub account. GHIDRA will be demoed at the RSA conference on March 5 and is expected to be released soon after on the agency's Code page and GitHub account.
The ‘creator’ of Bitcoin, Satoshi Nakamoto, is the world’s most elusive billionaire. Very few people outside of the Department of Homeland Security know Satoshi’s real name. In fact, DHS will not publicly confirm that even THEY know the billionaire’s identity. Satoshi has taken great care to keep his identity secret employing the latest encryption and obfuscation methods in his communications. Despite these efforts (according to my source at the DHS) Satoshi Nakamoto gave investigators the only tool they needed to find him — his own words. Using stylometry one is able to compare texts to determine authorship of a particular work. Throughout the years Satoshi wrote thousands of posts and emails and most of which are publicly available. According to my source, the NSA was able to the use the ‘writer invariant’ method of stylometry to compare Satoshi’s ‘known’ writings with trillions of writing samples from people across the globe. By taking Satoshi’s texts and finding the 50 most common words, the NSA was able to break down his text into 5,000 word chunks and analyse each to find the frequency of those 50 words. This would result in a unique 50-number identifier for each chunk. The NSA then placed each of these numbers into a 50-dimensional space and flatten them into a plane using principal components analysis. The result is a ‘fingerprint’ for anything written by Satoshi that could easily be compared to any other writing.
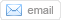
There have been rumors for years that the NSA can decrypt a significant fraction of encrypted Internet traffic. In 2012, James Bamford published an article quoting anonymous former NSA officials stating that the agency had achieved a “computing breakthrough” that gave them “the ability to crack current public encryption.” The Snowden documents also hint at some extraordinary capabilities: they show that NSA has built extensive infrastructure to intercept and decrypt VPN traffic and suggest that the agency can decrypt at least some HTTPS and SSH connections on demand. However, the documents do not explain how these breakthroughs work, and speculation about possible backdoors or broken algorithms has been rampant in the technical community. Yesterday at ACM CCS, one of the leading security research venues, we and twelve coauthors presented a paper that we think solves this technical mystery. The key is, somewhat ironically, Diffie-Hellman key exchange, an algorithm that we and many others have advocated as a defense against mass surveillance. Diffie-Hellman is a cornerstone of modern cryptography used for VPNs, HTTPS websites, email, and many other protocols. Our paper shows that, through a confluence of number theory and bad implementation choices, many real-world users of Diffie-Hellman are likely vulnerable to state-level attackers. For the nerds in the audience, here’s what’s wrong: If a client and server are speaking Diffie-Hellman, they first need to agree on a large prime number with a particular form. There seemed to be no reason why everyone couldn’t just use the same prime, and, in fact, many applications tend to use standardized or hard-coded primes. But there was a very important detail that got lost in translation between the mathematicians and the practitioners: an adversary can perform a single enormous computation to “crack” a particular prime, then easily break any individual connection that uses that prime. How enormous a computation, you ask? Possibly a technical feat on a scale (relative to the state of computing at the time) not seen since the Enigma cryptanalysis during World War II. Even estimating the difficulty is tricky, due to the complexity of the algorithm involved, but our paper gives some conservative estimates. For the most common strength of Diffie-Hellman (1024 bits), it would cost a few hundred million dollars to build a machine, based on special purpose hardware, that would be able to crack one Diffie-Hellman prime every year. Would this be worth it for an intelligence agency? Since a handful of primes are so widely reused, the payoff, in terms of connections they could decrypt, would be enormous. Breaking a single, common 1024-bit prime would allow NSA to passively decrypt connections to two-thirds of VPNs and a quarter of all SSH servers globally. Breaking a second 1024-bit prime would allow passive eavesdropping on connections to nearly 20% of the top million HTTPS websites. In other words, a one-time investment in massive computation would make it possible to eavesdrop on trillions of encrypted connections. NSA could afford such an investment. The 2013 “black budget” request, leaked as part of the Snowden cache, states that NSA has prioritized “investing in groundbreaking cryptanalytic capabilities to defeat adversarial cryptography and exploit internet traffic.” It shows that the agency’s budget is on the order of $10 billion a year, with over $1 billion dedicated to computer network exploitation, and several subprograms in the hundreds of millions a year. Based on the evidence we have, we can’t prove for certain that NSA is doing this. However, our proposed Diffie-Hellman break fits the known technical details about their large-scale decryption capabilities better than any competing explanation. For instance, the Snowden documents show that NSA’s VPN decryption infrastructure involves intercepting encrypted connections and passing certain data to supercomputers, which return the key. The design of the system goes to great lengths to collect particular data that would be necessary for an attack on Diffie-Hellman but not for alternative explanations, like a break in AES or other symmetric crypto. While the documents make it clear that NSA uses other attack techniques, like software and hardware “implants,” to break crypto on specific targets, these don’t explain the ability to passively eavesdrop on VPN traffic at a large scale. Since weak use of Diffie-Hellman is widespread in standards and implementations, it will be many years before the problems go away, even given existing security recommendations and our new findings. In the meantime, other large governments potentially can implement similar attacks, if they haven’t already.
|



 Your new post is loading...
Your new post is loading...








"There’s no backdoor in Ghidra," he said. "Come on, no backdoor. On the record. Scout's honor."